How Plural Uses MCP: Replacing Admin Tools with AI Chat Interfaces
When you're building a startup, every engineering decision carries weight. Do you assign a frontend engineer to build that Stripe subscription management interface? Do you create a custom admin panel for user permissions? The traditional approach is both time-consuming and resource-intensive, creating technical debt that can slow momentum when you need it most.
At Plural, we've taken a different path. Instead of building traditional internal tools, we've replaced them with MCP-powered chat interfaces that integrate directly with our existing codebase. This means we can handle complex admin tasks through natural language interactions, with JWT authentication and comprehensive audit logging built in.
This isn't just an experiment or proof of concept. We're using our own MCP implementation in production, managing everything from Stripe subscriptions to user permissions through conversational interfaces. If you want to streamline internal operations while maintaining enterprise-grade security and auditability, MCP is a practical alternative to traditional tooling.
The Internal Tooling Resource Drain
Most engineering teams know this story well: you need to manage user subscriptions, so someone builds a quick admin interface. Then you need user permission management, so the interface grows. Soon, you're maintaining multiple internal tools, each requiring frontend work, backend APIs, authentication flows, and ongoing maintenance.
The resource allocation challenge is real. You want your tools to work and be accessible to the entire team, but you don't want to consume a full frontend engineer to build them. For startups especially, every engineer hour spent on internal tooling is an hour not spent on core product development.
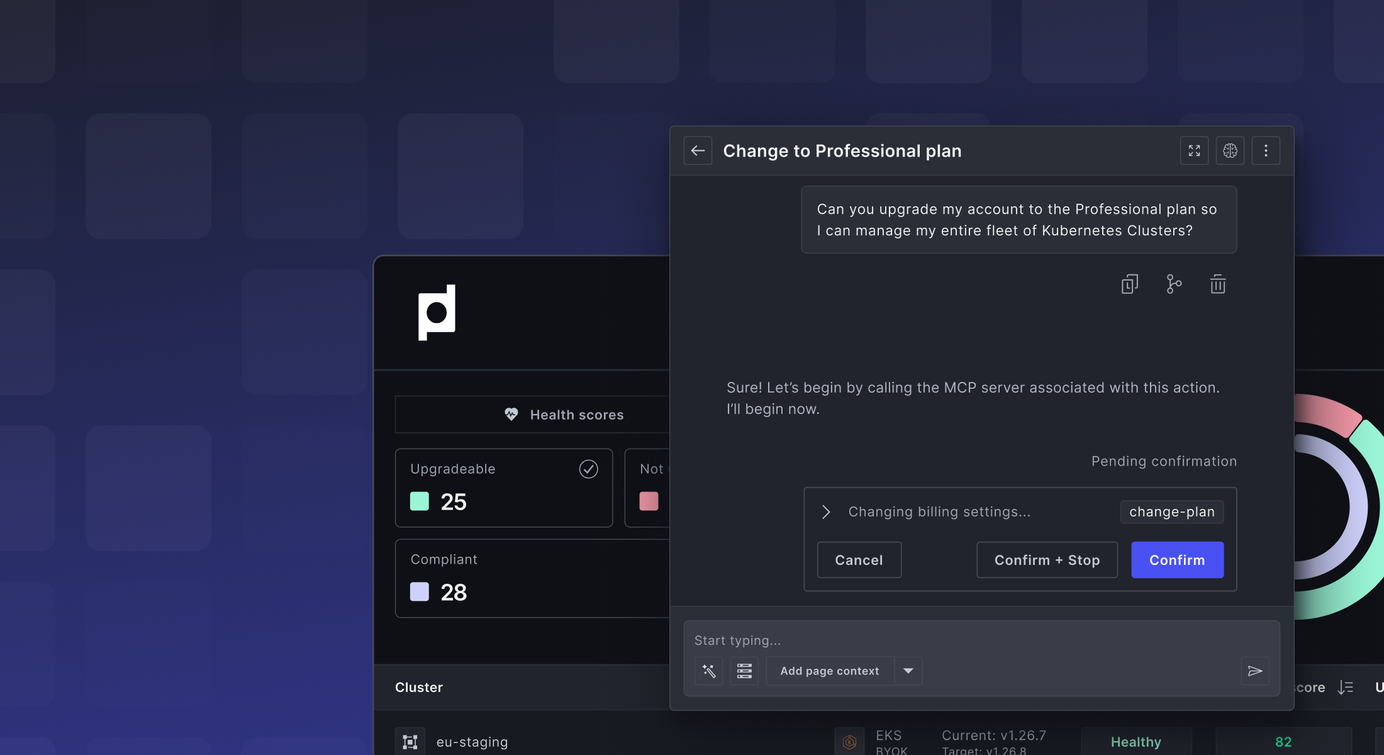
Plural's Chat-first Approach to Internal Tooling
Rather than building separate interfaces for each administrative function, we've embedded MCP servers directly into our existing infrastructure observability flows. The same chat interface that provides logs, alerts, and Kubernetes state information now handles subscription management, user permissions, and other administrative tasks through natural language commands.
The architecture is simple: MCP servers connect to the existing codebase and database connections, exposing specific functions through the chat interface. When a team member needs to check active Stripe plans or take action in Slack, they simply ask: "Show me our current subscription plans" or "Show me all the Slack channels I can interface with". The MCP server executes the appropriate database query and returns formatted results—no separate interface required.
This approach leverages Plural's existing authentication and authorization infrastructure. Since users are already authenticated in the platform, the MCP integration inherits those permissions and user context, eliminating the need for separate access management systems.
The development workflow remains familiar to engineers. MCP servers are defined within the same codebase, using existing libraries for database connections and business logic. This means that the same functions that power the core application can be exposed through the chat interface with minimal additional code.
Production-grade Security and Auditability
Security matters a lot when you're building conversational interfaces. Plural handles this with multiple layers of protection and monitoring.
JWT Authentication and Authorization
Each MCP server connection includes integrated JWT authentication using the ES256 algorithm with 15-minute token lifespans. When a user interacts with an MCP server through the platform, a JWT is dynamically generated containing the user's email and group memberships. This allows the MCP server to implement fine-grained authorization without maintaining separate user databases.
The implementation uses dynamic JSON Web Key Set (JWKS) retrieval for secure token validation:
def exchange(token) do
with {:ok, %{"kid" => kid}} <- peek_header(token),
{:ok, key} <- get_key(kid),
{:ok, claims} <- verify_and_validate(token, signer(key)) do
{:ok, claims}
end
The system fetches public keys from a .well-known/jwks.json endpoint and caches them for performance. This approach ensures that only authenticated Plural users can execute administrative functions, while the JWT claims provide context for role-based access control (RBAC) within the MCP server logic.
View the complete implementation: Plural's JWT module
Comprehensive Audit Logging
Every interaction with MCP servers is logged with full audit trails. The platform tracks which user executed which commands, when they were executed, and what the results were. This provides the same audit capabilities you'd expect from traditional admin interfaces, but with the added benefit of natural language context for each action.
Confirmation Workflows for Sensitive Operations
For high-risk operations, Plural implements optional confirmation workflows. Instead of automatically executing potentially destructive commands, the system can present a preview of the action and require explicit user confirmation before proceeding.
This helps teams balance convenience with safety, routine queries execute immediately, while sensitive modifications require deliberate approval. The confirmation interface shows exactly what will be executed, providing transparency before any changes are made.
Real-world Administrative Workflows
The practical benefits of MCP are obvious when looking at how we manage common administrative tasks.
Stripe Subscription Management
Managing subscription plans traditionally requires navigating to Stripe's dashboard or building custom interfaces. Through MCP, these operations become conversational:
- "List our current subscription plans" returns active plans with pricing details.
- "Add user@company.com to the enterprise plan" handles the subscription change and user notification.
- "Set up a 30-day trial for the pro plan" configures the trial parameters without manual Stripe configuration.
The underlying MCP tool implementation integrates directly with our existing database and serialization infrastructure:
def invoke(_) do
PlatformPlan.visible()
|> Repo.all()
|> Proto.serialize()
|> Jason.encode()
This approach reuses existing business logic and database connections rather than duplicating functionality in separate admin interfaces.
View the complete implementation: list_plans.ex
User Permission Management
User permissions and group management follow the same pattern. Commands like "Show users in the admin group" or "Remove user access from project X" execute through the same authorization systems that govern the core application, ensuring consistency across all access controls.
Trial Setup and Onboarding
New customer trials and onboarding workflows become simple conversational commands. "Create a trial for Company ABC with these requirements" can trigger complex provisioning workflows that would traditionally require multiple interface interactions.
The main advantage is that these workflows can be as sophisticated as needed on the backend while remaining simple to execute through natural language commands. Complex business logic is encapsulated in the MCP server functions rather than exposed through complicated user interfaces.
Developer Experience and Operational Benefits
The shift to MCP-powered internal tooling has created several unexpected advantages beyond the obvious resource savings.
Integration with Existing Development Workflows
Since MCP servers are defined within the existing codebase, they benefit from the same development practices as the core application. Functions can be unit tested, code reviews apply to administrative logic, and deployments follow the same CI/CD pipelines.
This integration eliminates the common problem of administrative tools becoming stale or unreliable due to separate maintenance cycles. When the core application evolves, the MCP interfaces automatically evolve with it.
Reduced Cognitive Overhead
Team members no longer need to remember different interfaces, authentication methods, or workflows for various administrative tasks. The same chat interface that provides infrastructure insights also handles subscription management, user permissions, and other operational needs.
This consolidation reduces onboarding time for new team members and eliminates the context switching that typically slows administrative workflows.
Faster Iteration and Testing
Modifying administrative workflows becomes as simple as updating function logic and redeploying the application. There's no separate frontend to update, no additional API endpoints to modify, and no interface-specific testing required.
The natural language interface also makes it easy to test workflows with stakeholders who might not be comfortable navigating traditional admin interfaces. Product managers and customer success teams can validate administrative processes through the same conversational interface they'll use in production.
Enhanced Auditability and Compliance
The comprehensive logging of all MCP interactions creates detailed audit trails that are often superior to traditional admin interfaces. Every command includes full context about who executed it, when, and what the results were—information that's often incomplete in custom admin tools.
This detailed logging becomes particularly valuable for compliance scenarios where organizations need to demonstrate proper access controls and administrative oversight.
When MCP Internal Tooling Makes Sense
While Plural's approach demonstrates MCP's potential for internal tooling, it's not a universal solution for every organization or use case.
Startups and growth-stage companies benefit most from the resource allocation advantages. The ability to implement sophisticated administrative workflows without dedicated frontend engineering resources allows teams to focus on core product development. The rapid iteration capability becomes particularly valuable when administrative requirements are still changing, which requires significant interface modifications in traditional tools, but can be implemented as simple function updates in MCP servers.
Enterprise organizations with established internal tooling practices may find MCP more valuable for supplementing existing systems rather than replacing them entirely. The audit logging and security features make MCP suitable for enterprise environments, but integration with existing identity management and compliance systems requires careful planning. The conversational interface can be particularly valuable when administrative tasks are performed by non-technical stakeholders who would benefit from natural language interactions.
Technical prerequisites for MCP implementation include teams comfortable with backend development and API integration. While frontend complexity is eliminated, the backend logic still requires careful design and implementation. Organizations need a robust logging and monitoring infrastructure to fully utilize MCP's audit capabilities, and the security benefits depend on proper JWT implementation and integration with existing authentication systems. MCP works best when there's already a strong foundation of business logic and data access patterns that can be exposed through MCP servers.
Getting Started with MCP Internal Tooling
For organizations interested in exploring MCP for internal administrative tasks, start with low-risk, high-value use cases. Begin with read-only operations like subscription status checks or user permission queries—these tasks provide immediate value while teams become comfortable with the MCP development workflow.
Focus on operations that currently require context switching between multiple interfaces. If team members regularly bounce between Stripe, user management systems, and custom admin panels, those workflows are prime candidates for MCP consolidation. Invest in comprehensive logging and audit capabilities from the beginning, as retrofitting observability is more complex than building it in initially.
Consider confirmation workflows for operations that modify data or trigger external actions. The flexibility to require explicit approval for sensitive commands provides an important safety net as teams adapt to conversational administrative interfaces.
The future of internal tooling increasingly points toward AI-native approaches that eliminate traditional interface complexity while maintaining enterprise-grade security and auditability. Plural's production implementation demonstrates that this future is not just possible—it's practical for organizations willing to rethink how administrative workflows should work in an AI-first world.
Newsletter
Join the newsletter to receive the latest updates in your inbox.









