Introducing Plural Compliance Reports: Kubernetes Security Made Simple
Plural now offers built-in compliance reporting that gives you a complete view of your Kubernetes security posture across your entire fleet.
For organizations running Kubernetes at scale, maintaining compliance across
clusters presents a significant challenge. Security and platform teams face a
common struggle: how do you efficiently verify that all your clusters have the
necessary security software installed and are free from critical
vulnerabilities?
The traditional approach is both time-consuming and error-prone. Teams must
authenticate to each cluster individually to check for required components. Many
organizations lack a comprehensive registry of all their clusters, making it
difficult to even know where to look. Critical security information remains
scattered across different systems, and generating reports for security audits
requires extensive manual data processing.
This becomes particularly problematic for companies in regulated industries,
where demonstrating compliance isn't just good practice—it's a requirement.
InfoSec teams need reliable, comprehensive data about what's running across all
Kubernetes environments.
Now Available: Plural Compliance Reports
Plural now offers built-in compliance reporting that gives you a complete view
of your Kubernetes security posture across your entire fleet. With a few clicks,
you can generate comprehensive reports showing all security-related software
installed on your clusters, current vulnerability status across your
environment, and verification that your clusters meet your organization's
security policies.
Key Features
Fleet-Wide Visibility
Compliance Reports provide a consolidated view of critical security components
across all your clusters. This includes policy scanners, CVE scanners,
observability agents, networking software, and other security policy
requirements. This eliminates the need to authenticate to each cluster
individually and manually compile information.
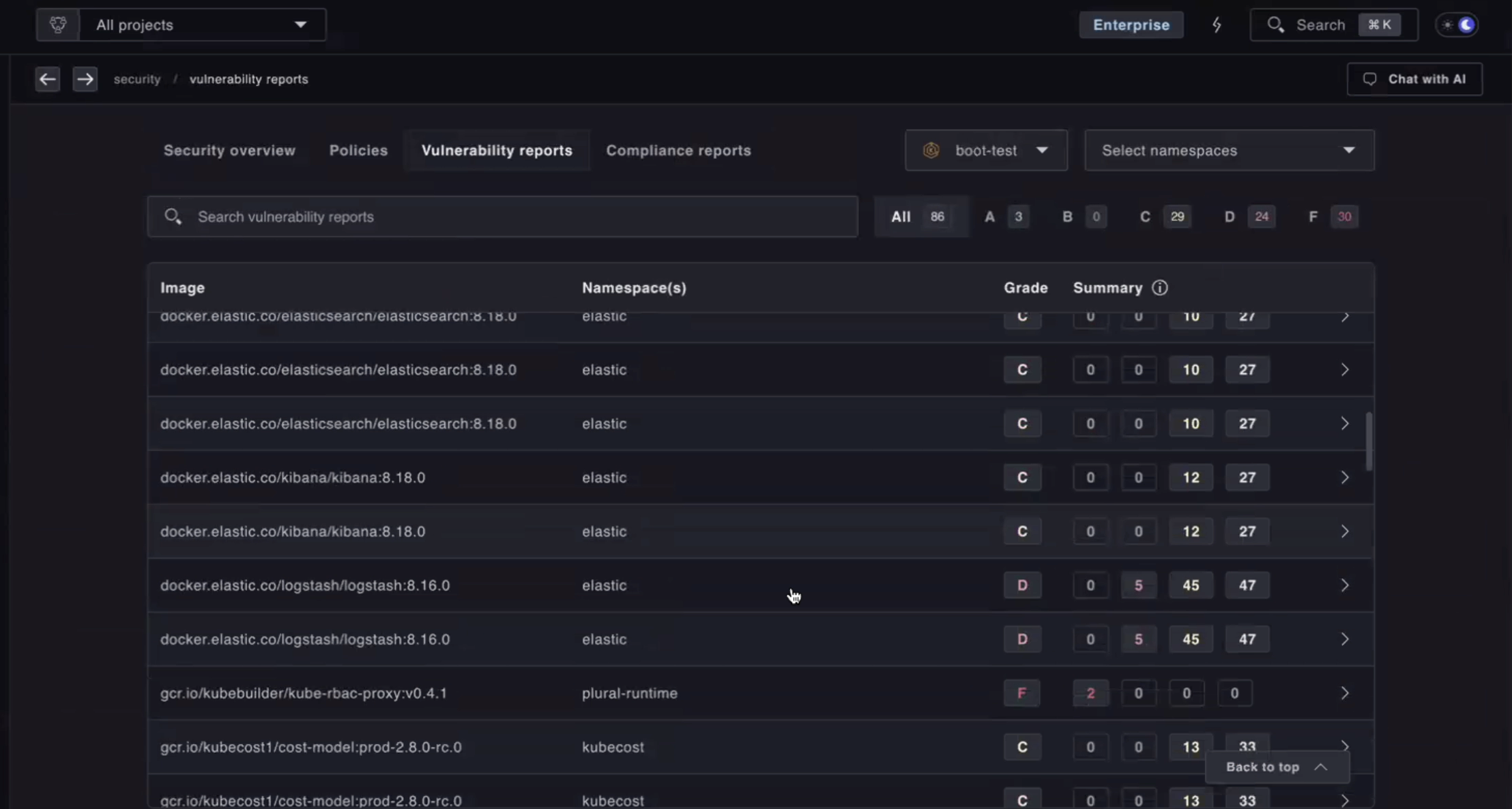
Comprehensive Vulnerability Reporting
Beyond just software inventory, Compliance Reports include detailed
vulnerability data. You can view all CVEs present in your environment,
understand their severity levels, and track vulnerability age to identify
long-standing issues that need attention. This informaton is also surfaced under the Security > Vulnerability Reports tab in the Plural console.
Simple Export Process
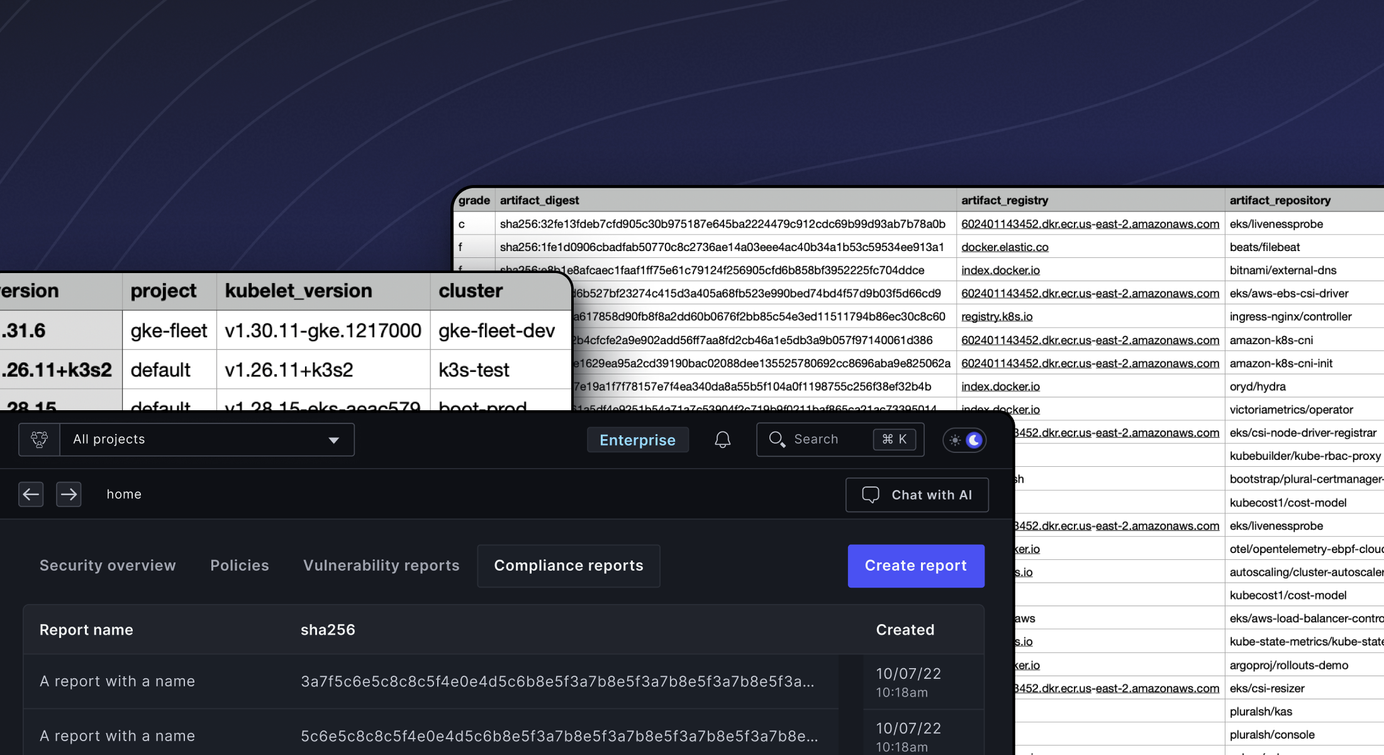
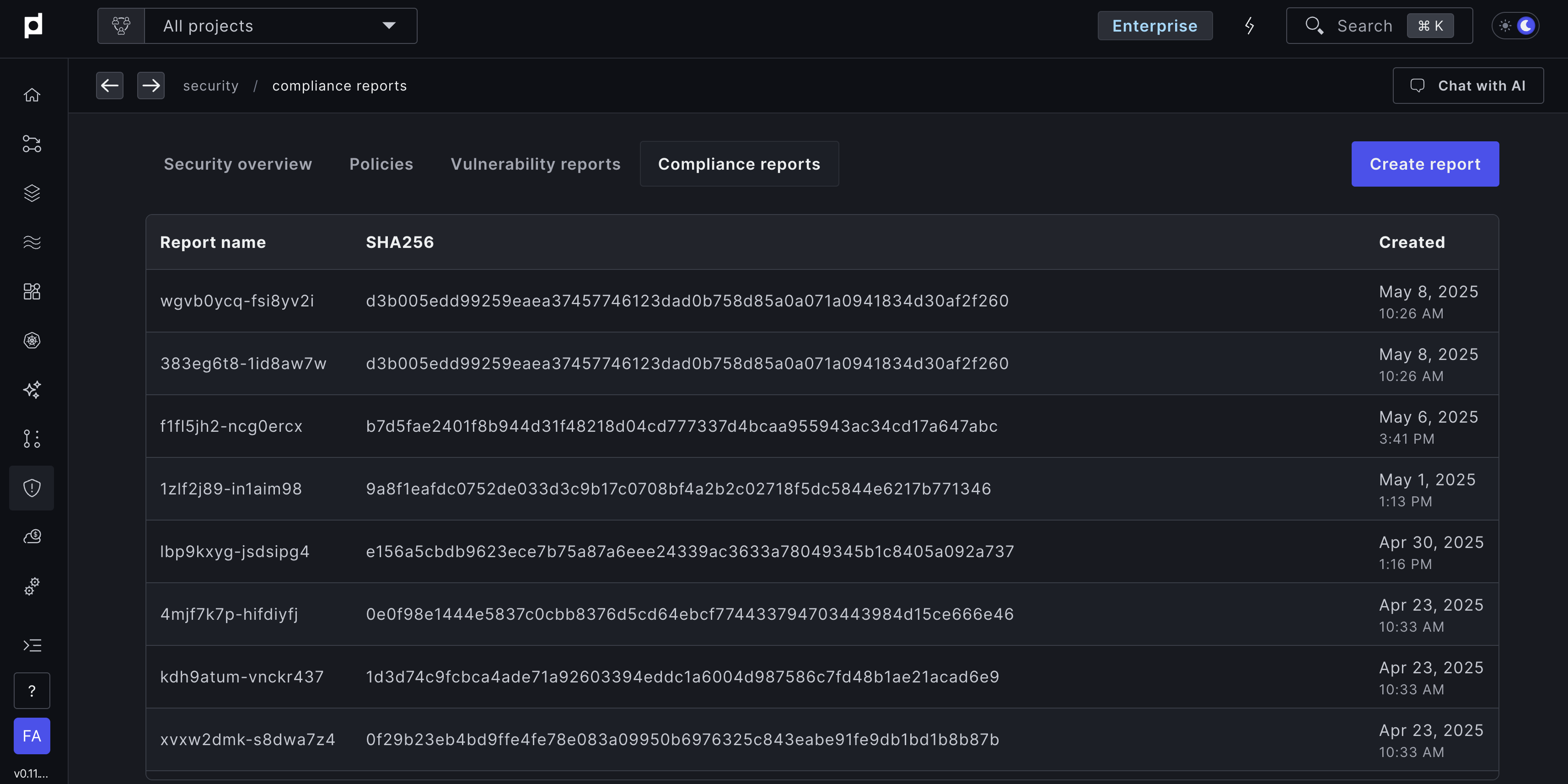
To generate a report, navigate to Security > Compliance reports in the Plural console,
click "Create Report," and download a ZIP file containing all compliance data.
When you unzip the file, you'll have access to individual CSVs for clusters,
services, and vulnerabilities.
How It Works
Compliance Reports leverage data already collected by Plural's management
platform. Plural maintains a complete inventory of what's installed across your
clusters and continuously collects CVE data from all managed clusters. When you
request a report, Plural compiles this data into standardized CSV files and
generates a unique name and SHA-256 hash for verification.
The result is a comprehensive compliance snapshot that can be easily shared with
security teams or auditors.
Real-World Use Cases
Some real-world use cases where Plural's compliance reports can help:
Federal and Government Compliance (FedRAMP, NIST 800-53)
Government agencies and their contractors must adhere to strict security
controls defined by FedRAMP and NIST frameworks. Compliance Reports help these
organizations:
- Document the presence of required security controls across all Kubernetes
clusters - Verify that vulnerability scanning is active on all workloads
- Demonstrate that critical vulnerabilities are remediated within required
timeframes (typically 30 days for critical findings) - Meet specialized GovCloud requirements for isolated, dedicated infrastructure in AWS and Azure environments designed specifically for sensitive government workloads
Healthcare (HIPAA, HITRUST)
Healthcare organizations processing Protected Health Information (PHI) must
maintain strict security controls:
- Verify encryption tools are properly deployed across all clusters handling
patient data - Document access controls and network segmentation for PHI-containing workloads
- Track vulnerability remediation timelines to meet HITRUST certification
requirements - Generate evidence for annual security assessments and audits
Financial Services (SOC 2, PCI DSS)
Financial institutions face some of the most rigorous compliance requirements:
- Demonstrate proper network segmentation for cardholder data environments
- Verify that all clusters processing financial data have appropriate security
controls - Document vulnerability management processes for SOC 2 Type 2 audits
- Provide evidence that critical security patches are applied within required
timeframes - Support quarterly PCI compliance reviews with comprehensive security posture
reports
What's Next
While the current implementation supports CSV format, we're working on expanding
output options. Future releases will include PDF reports for easier sharing with
non-technical stakeholders and JSON format for programmatic integration with
other systems.
The Plural Advantage
What sets Plural's Compliance Reports apart is our integration with our
comprehensive Kubernetes management platform. Unlike standalone tools, Plural
already has visibility into all your clusters, making report generation simple
and reliable.
We've deliberately designed Compliance Reports to be deterministic and
verifiable. When it comes to compliance, you need to know exactly what's
installed across all your clusters and be 100% confident in the accuracy of that
information.
Try Compliance Reports Today
Ready to simplify your Kubernetes compliance verification? Book a demo to see how compliance reports can
help your organization maintain security standards across your Kubernetes fleet,
or sign up to try Plural today.
For more information about Plural's security features, visit our
security documentation.
Newsletter
Join the newsletter to receive the latest updates in your inbox.